In today's rapidly evolving digital landscape, advanced copyright identification documents pose a significant threat to legal systems. The increase of scannable copyright presents serious hurdle in preventing fraud, identity theft, and other unlawful activities. To effectively counteract this growing problem, it is essential to implement comprehensive security measures and tactics.
This necessitates a multi-faceted approach that includes collaboration between government agencies, technology providers, and the citizens.
Revolutionizing Identity Verification with AI: ID Scanning of the Future
As technology rapidly evolves, so too do the methods we use to verify identity. AI-powered ID scanning is emerging as a revolutionary solution, offering enhanced security and efficiency in a world increasingly reliant on digital transactions and interactions. This innovative approach leverages machine learning algorithms to interpret images of identification documents with unprecedented accuracy. By automating the verification process, AI-powered ID scanning can significantly decrease human error, optimize workflows, and mitigate fraud in real time.
The benefits of AI-powered ID scanning extend across a broad range of industries. Financial institutions, government agencies, and even healthcare providers can leverage this technology to confirm the authenticity of user documents, fortify security protocols, and provide a seamless experience for customers.
- Furthermore, AI-powered ID scanning can be integrated with other systems to develop comprehensive identity management solutions. By combining biometric data with document verification, organizations can achieve a higher level of detail and certainty in their identity verification processes.
Nevertheless, it's crucial to tackle the ethical implications associated with AI-powered ID scanning. Ensuring data privacy and compliance with relevant regulations are paramount. By prioritizing transparency, user consent, and responsible development practices, we can harness the power of AI to create a more secure and effective future for identity verification.
Youth Exposure to Forbidden Material: The Technology-Driven Menace
The digital age conjures a unique challenge: underage access to restricted content. Whilethe internet provides countless opportunities for learning and growth, it also serves as a portal to harmful content. Technology's rapid evolution has only magnified this threat, making it vital to address the issue with stringent strategies.
- Additionally, the rise of interactive online spaces
- often lack adequate safeguards to prevent minors from encountering
- problematic material.
This explosion of unrestricted content can have , potentially impacting their emotional well-being, social development, and overall safety. This concerted action is essential to minimizing the risks posed by underage access to restricted content in our increasingly digital world.
The Evolution of copyright Identification: Can AI Keep Up
The fight against copyright goods has always been a significant challenge for businesses and consumers alike. From forged banknotes to replica designer handbags, the methods used to create fake products are constantly evolving. To combat this ever-growing threat, identification technologies have also undergone a rapid evolution, with artificial intelligence (AI) emerging as a potential game-changer. AI algorithms can analyze images and data at an unprecedented speed and accuracy, making them ideal for detecting subtle differences between genuine and copyright items. However, the question remains: can AI truly keep pace the ingenuity of counterfeiters?
Counterfeiters are notorious for their resourcefulness, constantly refining their techniques to Underage Access evade detection. They may utilize advanced printing methods, incorporate complex materials, or even manipulate digital images to create highly plausible counterfeits. This means that AI systems must be regularly improved to remain effective.
The future of copyright identification likely lies in a combination of technologies, with AI playing a crucial role. By integrating AI with other methods such as blockchain technology, we can create a more robust and comprehensive system for combating counterfeiting. It will require ongoing collaboration between researchers, industry experts, and policymakers to ensure that AI remains one step ahead of the ever-evolving threat of counterfeits.
The Clash of Scannable Fakes and Intelligent Verifiers
The digital realm is rapidly evolving, with new threats emerging at an alarming rate. Among these threats, deepfakes pose a significant challenge to security and trust. These meticulously crafted fabrications can deceive even the most discerning eye, making it increasingly difficult to distinguish reality from simulation. In response to this growing danger, intelligent verifiers are being developed to combat these sophisticated manipulations.
This ongoing battleground between deepfakes and intelligent detection systems is a race against time. As technology progresses, so too do the capabilities of both sides. The future of security depends on our ability to stay ahead of the curve and develop ever more sophisticated methods for detecting and preventing misinformation.
Addressing the Legal and Ethical Implications of AI in ID Scanning
The exponential advancement of artificial intelligence (AI) has opened up new horizons in various fields, including identity verification. While AI-powered ID scanning delivers numerous benefits, such as increased accuracy and productivity, it also presents a host of legal and ethical issues.
Regulators are grappling to develop comprehensive frameworks to govern the deployment of AI in ID scanning, reconciling the need for security with the protection of data security.
- A key ethical issue is the possibility of discrimination in AI algorithms, which could result discriminatory outcomes.
- Furthermore, there are concerns about the storage of sensitive personal data by AI systems and the exposure to hacks.
Navigating these complex legal and ethical obstacles requires a collaborative effort involving technologists, policymakers, ethicists, and the public.
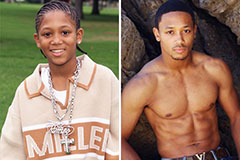 Romeo Miller Then & Now!
Romeo Miller Then & Now! Andrew Keegan Then & Now!
Andrew Keegan Then & Now!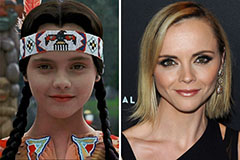 Christina Ricci Then & Now!
Christina Ricci Then & Now! Gia Lopez Then & Now!
Gia Lopez Then & Now! Talia Balsam Then & Now!
Talia Balsam Then & Now!